Back in October last year I was out in New York for the Hardware Innovation Workshop and Maker Faire New York where I took part in a panel discussion along with Massimo Banzi and Jason Kridner—and chaired by MAKE's Dale Dougherty—on what's in store for micro-controllers, and what the next generation of board could bring.
The often deranged postings of yet another hacker, pretending to be an Astronomer, pretending to be a hacker who has written a book or two for O'Reilly Media.
Sunday, January 05, 2014
Hacking the CES Scavenger Hunt
It has just been announced that at this year's Consumer Electronics Show (CES) will feature a promotional scavenger hunt based around Apple's iBeacon technology. What if you could win the hunt, without ever having to go to CES?
 |
| What if you could win the hunt, without ever having to go to CES? |
Quietly introduced by Apple at WWDC last year, iBeacon is a technology that allows you to add real world context to smart phone applications. Based around Bluetooth LE—part of the new Bluetooth 4.0 standard—it’s a way to provide basic indoor navigation and proximity detection.
As we talked about when we reverse engineered the Estimote beacons, there are three properties of an iBeacon that work together to create the beacon’s identity. These are:
- UUID — This is a property which is unique to each company, in most use cases the same UUID would be given to all beacons deployed by a company (or group).
- Major — The property that you use to specify a related set of beacons, e.g. in a retail setting all the beacons in one store would share the same Major value.
- Minor — The property that you use to specify a particular beacon in a location.
The scavenger hunt is therefore a hunt for a number of beacons that will probably all share the same UUID and Major numbers, but will have different Minor numbers. Effectively, we're looking for a set of beacons.
However wandering the hallways at CES hoping to get into the—approximate 100 foot range—of all of the iBeacons they've scattered across the show floor sounds like a lot of work.
CES has teamed up with Radius Networks who are providing the iBeacon hardware, and Marc Wallace—CEO and cofounder of Radius Networks—has this to say about the hunt,
This is one of the coolest proximity-aware apps we have worked on. This is also one of the first, tangible applications that leverages iBeacon technology. And it is a great example of how iBeacon technology is not just about advertising as it is about bringing new and innovative solutions to the marketplace. We are very excited to be a part of it.
Since they're using hardware from Radius Networks we can't just assume—as we could with the Estimote hardware—that we know the UUID of the beacons. However the identities of the beacons—all of the beacons—are somewhere where we can easily get our hands on them, the CES mobile app.
Sure enough looking at the CES Android application—it's fairly easy just to download the APK without having to install—there are some hints there for us and using a decompiler it was fairly easy to find the details of the target beacons.
 |
| The Minor numbers of the nine target beacons in the code of the CES mobile application. |
The iBeacon UUID we're looking for is 842AF9C4-08F51-1E39-282F-23C91AEC05E, while the Major number—interestingly not actually needed and just ignored by the Android application—is 65000, while the nine beacons scattered throughout the CES venue have Minor numbers from 65001 to 65009.
 |
| An almost completed scavenger hunt—with eight of the nine beacons already "found." |
Since we now know the identities of the beacons, it's trivial to finish the scavenger hunt without ever going to CES as it's actually fairly simple to build your own iBeacon hardware and "fake" the app into thinking you've found the beacons. To do that you can either use a Raspberry Pi, or a Bluetooth LE board like the Red Bear Labs BLE Mini board—Radius Networks, the people supplying the hardware to CES, is even selling a "iBeacon Development Kit" which would work just fine for our purposes.
At which point—now you have your own iBeacon hardware—you can just go ahead and set the UUID, Major and Minor numbers of your beacon to each of the CES scavenger hunt beacon identities in turn, and then bring your beacon into range of your cell phone running which should be running the CES mobile app. Once you've shown the app all of the beacons, you'll have "finished" the scavenger hunt and can claim your prize. Of course doing that isn't legal. It's called fraud and will probably land you in serious trouble.
Of course it could be worse. If they are using Estimote hardware it'd be easy for someone to make the hunt impossible to complete. Because as we've shown, anyone with the Estimote SDK can modify the UUID, Major and Minor number of the Estimote beacons in the field. Which would have meant that the beacons deployed across the CES floor didn't work for the scavenger hunt anymore.
We talked about both of the ability to configure "fake" beacons, and the ability to disable beacon in the field—in our discussion of our reverse engineering of the Estimote iBeacon hardware. However, we didn't think we'd see something like this quite as soon.
The Snapchat Leak
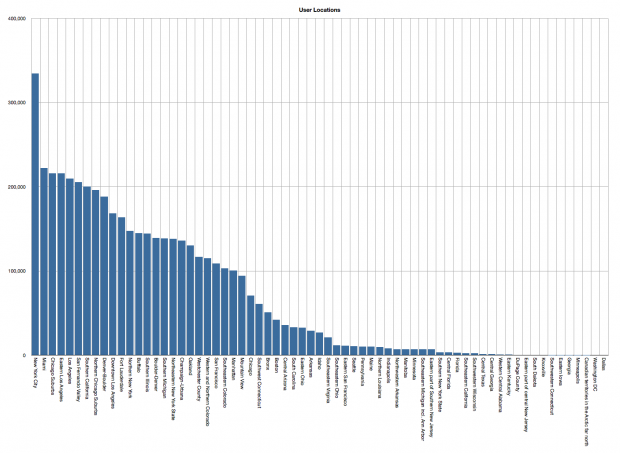 |
| The number of Snapchat users by geographic location. Users are predominately located in New York, San Francisco and the surrounding greater New York and Bay Areas. |
Theoretically, if someone were able to upload a huge set of phone numbers, like every number in an area code, or every possible number in the U.S., they could create a database of the results and match usernames to phone numbers that way.
Adding that they had various "safeguards" in place to make it difficult to do that. However it seems likely that—despite being explicitly mentioned in the initial report four months previously—none of these safeguards included rate limiting requests to their server, because someone seems to have taken them up on their offer.